A policy is an entity that defines the rules and conditions associated with security components, which are applied to a program under criteria that comply with regulatory frameworks for information protection.
The definition and configuration of security policies allow the establishment of mechanisms for diagnosis, control and protection of information at different levels.
Who Sets the Policies
The Administrator and Specialist are the roles established in ASEC that will be able to define the criteria for compliance with policies.
Policy structure
A policy at Aranda Security is composed of the following criteria
- Basic Facts: Basic policy information such as name, status, description, and monitoring time.
-
Configuration criteria: Each policy in Aranda Security groups the required security applications or components on a workstation, into categories according to their function. The Enabled criteria in ASEC they are: ANTIMAWARE, ANTIPISHING, BACKUP, CLOUD STORAGE, COMMUNICATIONS TOOLS, DATA LOSS PREVENTION, ENDPOINT ENCRYPTION, FIREWALL, HEALTH AGENT, REMOTE CONTROL, VIRTUAL MACHINE, VPN CLIENT and WEB BROWSER.
Note: To understand the scope of the validations by each of the security programs that group the ASEC policy criteria, according to the operating system (Windows, Linux and Mac), know How to View the Security Application Listing - Validations: These are the parameters responsible for verifying, according to the program chosen by configuration criteria, compliance with security policies in each of the workstations. Validations by configuration criteria.
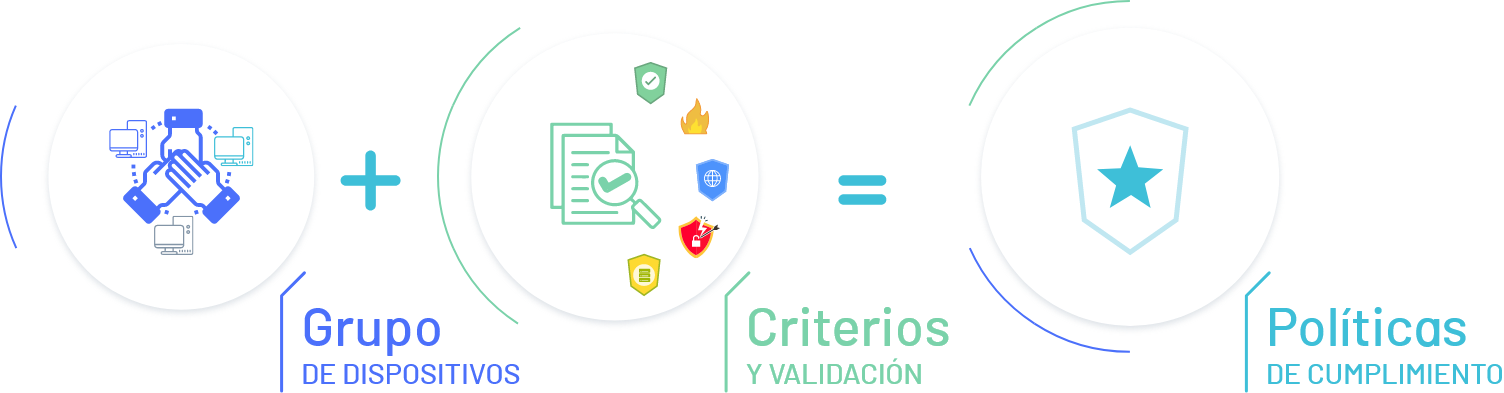
- Device Groups: Grouping of devices linked to the ASEC agent, to be associated with the compliance policy.
In the Policies section of the Aranda Security Compliance console, you will be able to Define compliance policies.
What does a policy do on a device?
Establishes security guidelines to detect and respond to potential vulnerabilities


