The policies configured in Aranda Security evaluate the compliance levels of security applications on different workstations. This diagnosis is possible due to the validations that are applied for the different policy criteria programs
For each security program, different validation options will be activated.
Each validation may be used in the Policy criteria Available.
The validation options available in Aranda Security are:
⚐ Note: To understand the scope of the validations by each of the security programs that group the ASEC policy criteria, according to the operating system (Windows, Linux and Mac), know How to View the List of Security Applications.
Here are some scenarios for configuring policy criteria and validations:
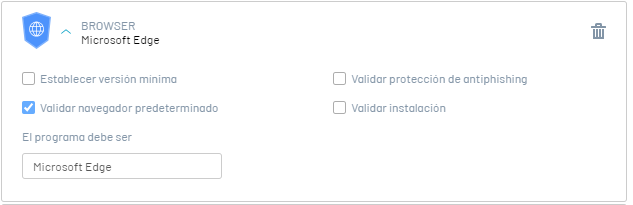
1. Validate default browser
This option validates that the selected browser is set as the default browser on the workstation. The validation response options are:
| Return |
Description |
| MEETS |
If the browser is set as default on the workstation. |
| NOT COMPLIANT |
If the browser is not set as default or if it is not installed |
| Example |
It is validated on the workstation if the Microsoft Edge is set as default. |
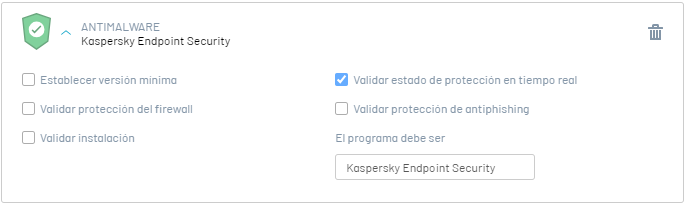
2. Validate Protection Status in Real-Time
This option validates that the software has real-time protection enabled. The validation response options are:
| Return |
Description |
| MEETS |
Whether the software has real-time protection enabled. |
| NOT COMPLIANT |
If the software does NOT have real-time protection enabled or if it is not installed. |
| Example |
It is validated that the software Kaspersky Endpoint Security have real-time protection enabled. |
3. Validate Execution Status
This option validates whether the software is running on the workstation. The validation response options are:
| Return |
Description |
| MEETS |
If the software is running. |
| NOT COMPLIANT |
if the software is NOT running or if it is not installed. |
| Example |
It is validated if the Software Norton Antivirus is running. |
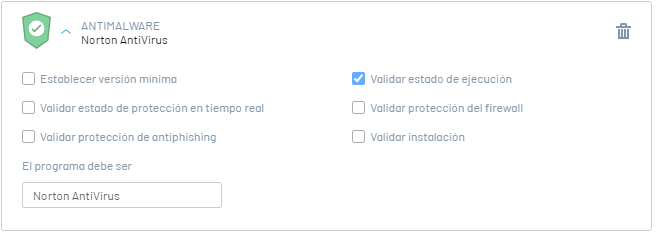
4. Validate Installation
This option is valid if the software is installed on the workstation. The validation response options are:
| Return |
Description |
| MEETS |
If the software is installed. |
| NOT COMPLIANT |
if the software is NOT installed. |
| Example |
It is validated if the Software Norton Antivirus It is installed on the workstation. |
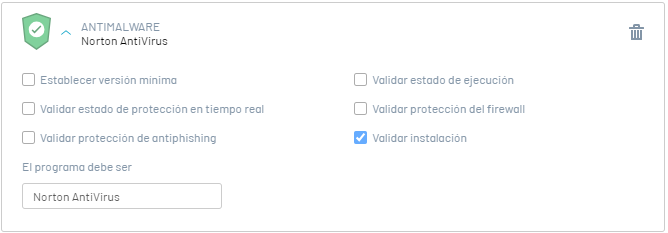
5. Validate Firewall Protection
This option is valid if the software has FIREWALL protection enabled. The validation response options are:
| Return |
Description |
| MEETS |
If the software has FIREWALL protection enabled. |
| NOT COMPLIANT |
If the software does NOT have FIREWALL protection enabled or if it is NOT installed. |
| Example |
Validate that the software Windows Firewall have FIREWALL protection enabled. |
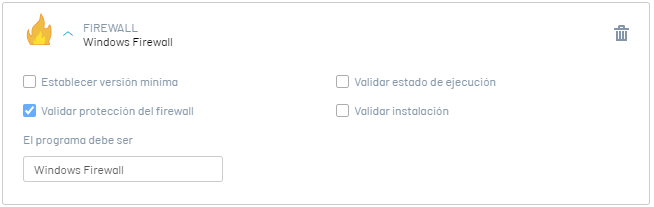
6. Validate Anti-Phishing Protection
This option is valid if the software has Anti-Phishing protection enabled. The validation response options are:
| Return |
Description |
| MEETS |
If the software has Anti-Phishing protection enabled. |
| NOT COMPLIANT |
If the software does NOT have Anti-Pishing protection enabled or if the software is NOT installed. |
| Example |
Validate that the software Google Chrome have Anti-Phishing protection active. |
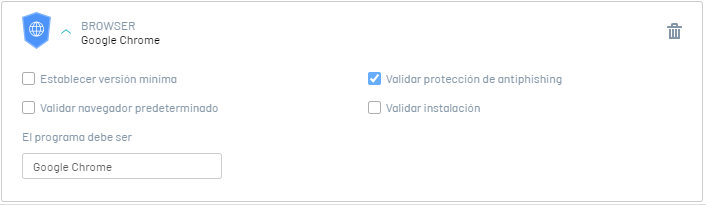
7. Set Minimum Version
This option sets a minimum version to later validate against the version
installed on the workstation. The validation response options are:
| Return |
Description |
| MEETS |
This criterion is met when a full version is specified or when the version is greater than a partial version |
| NOT COMPLIANT |
The criterion is not met when the installed software has a different or lesser version, depending on the case. |
| Example |
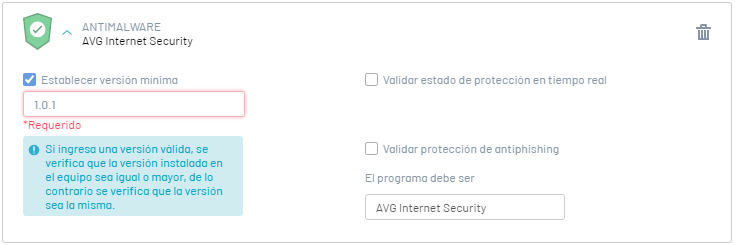
Validate that the version of AVG internet security installed on the workstation is greater than or equal to version 1.0.1 |
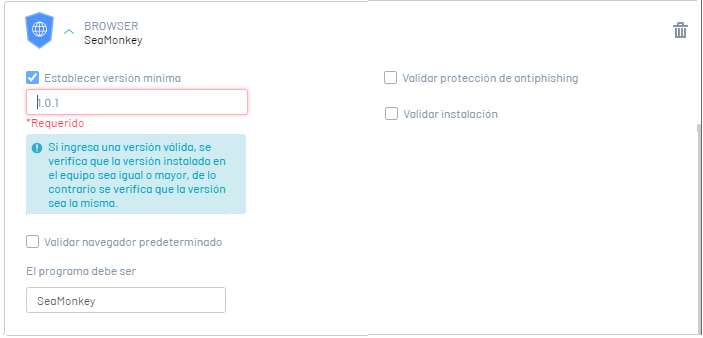
|Example|Validate that the version of Sea Monkey installed on the workstation is greater than or equal to version 1.0.1
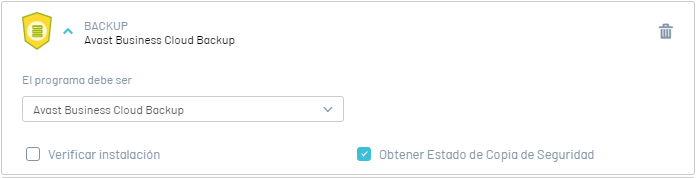
8. Validate Backup Status
This option validates the status of the software backup. The validation response options are:
| Return |
Description |
| MEETS |
If the software has the option to get the backup status enabled. |
| NOT COMPLIANT |
If the software does NOT have the option to get the backup status enabled. |
| Example |
Validates that the backup status of the software can be obtained Avast Business Cloud Backup . |