1. In the Policy information view in Aranda Security Compliance, on the Groups You will be able to view the list of groups associated with the policies. Selecting a group with associated devices will allow you to display the Devices with the detail of compliance of the devices.
2. In the window Devices You will be able to view the related information of the devices associated with a group. This data is organized by name, operating system, IP, start date, and remediation action to be executed of the group’s compliance level.
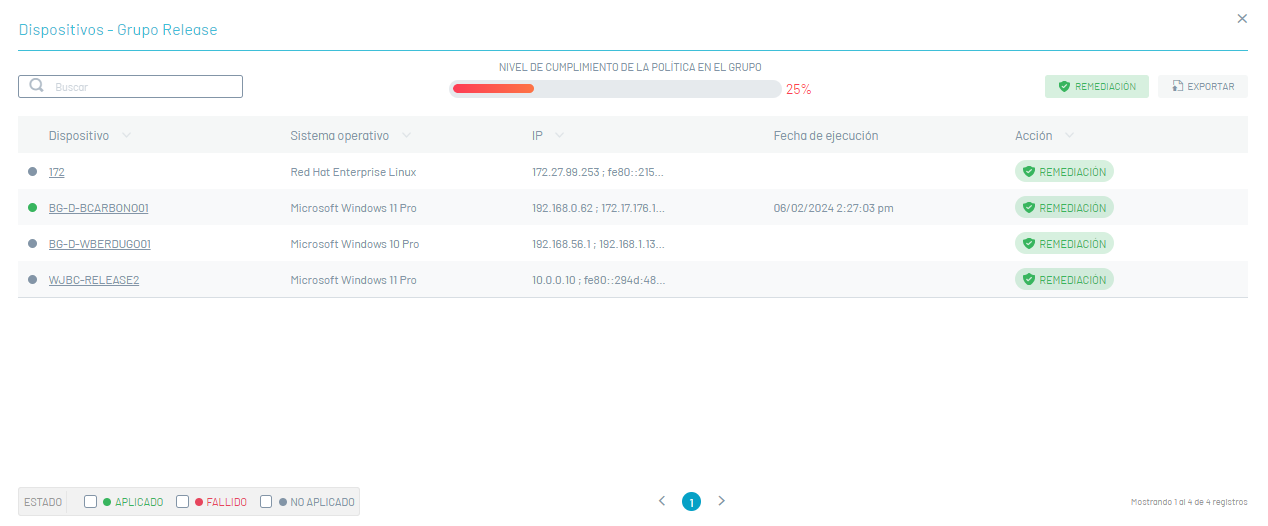
3. By selecting the device name, you can view in detail relevant information such as device name, policy name, the date of the scan, group to which it belongs, and applied policy criteria.
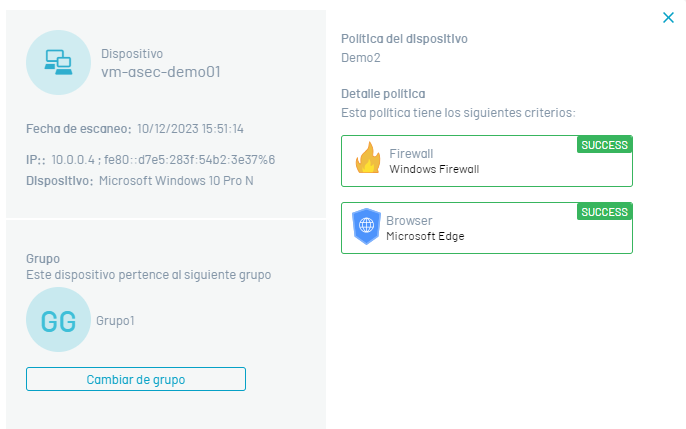
4. The detail of the policy applied to the device will be able to visualize the level of compliance with the criteria of the implemented policies, through the referenced States:
| States | Description |
|---|---|
| SUCCESS | The Successful status is displayed when the policy criterion is met, applied to the device. |
| FAILED | The failed status is displayed when the policy criterion, applied to the device, is NOT met |
| NOT APPLIED | The Not Applicable status is displayed when the device has not been scanned. |
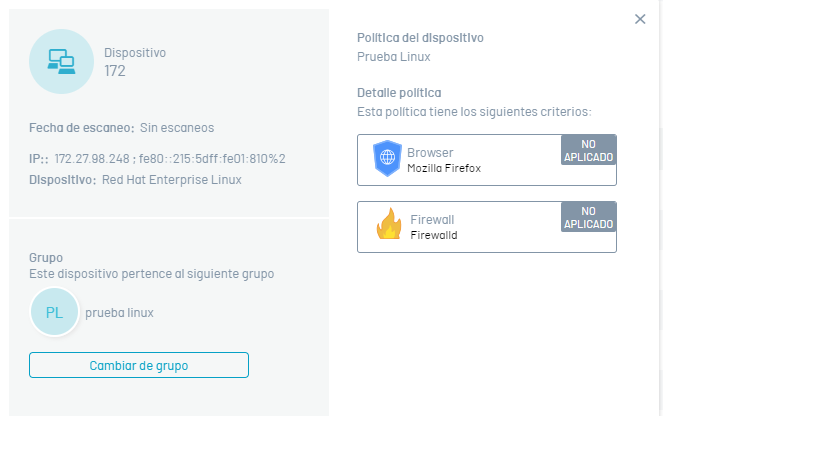
5. In the policy detail, selecting the generated state displays the case validations.
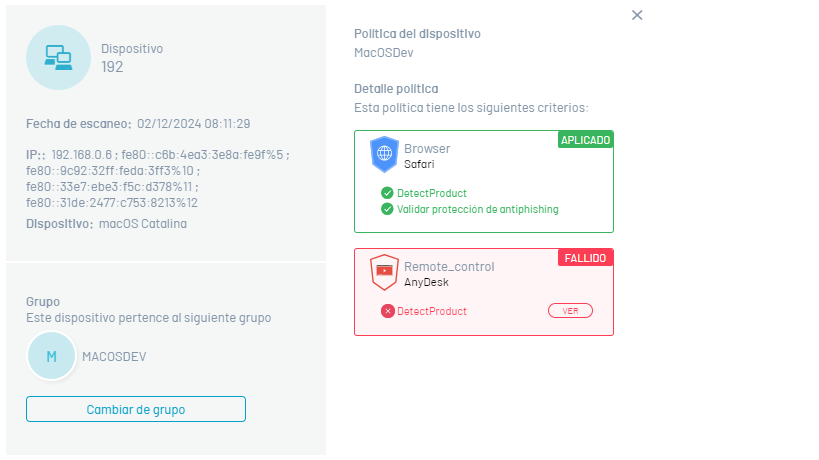
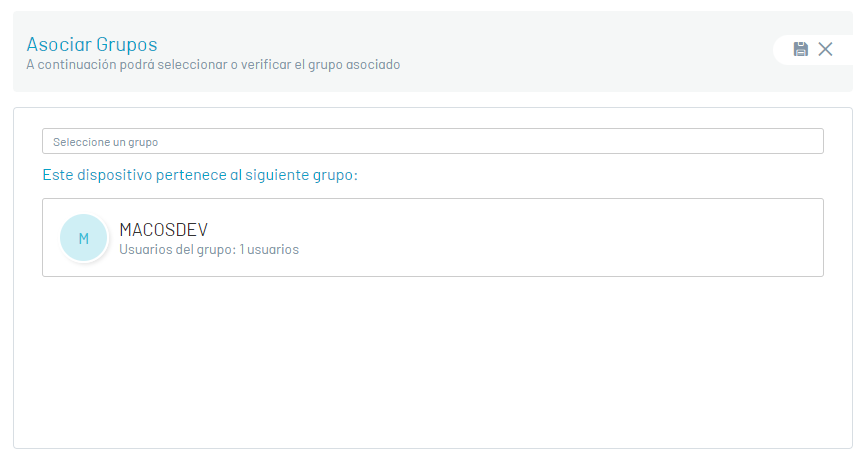
⚐ Note: In the device detail select the Change Group to modify the existing group association.
Remediation Actions
6. Regardless of the status generated (Successful, Failed, or Not Applicable) during the policy compliance analysis on the devices, you will be able to execute the required remediation actions. Select the Remediation to execute the actions enabled for the implemented security criterion.
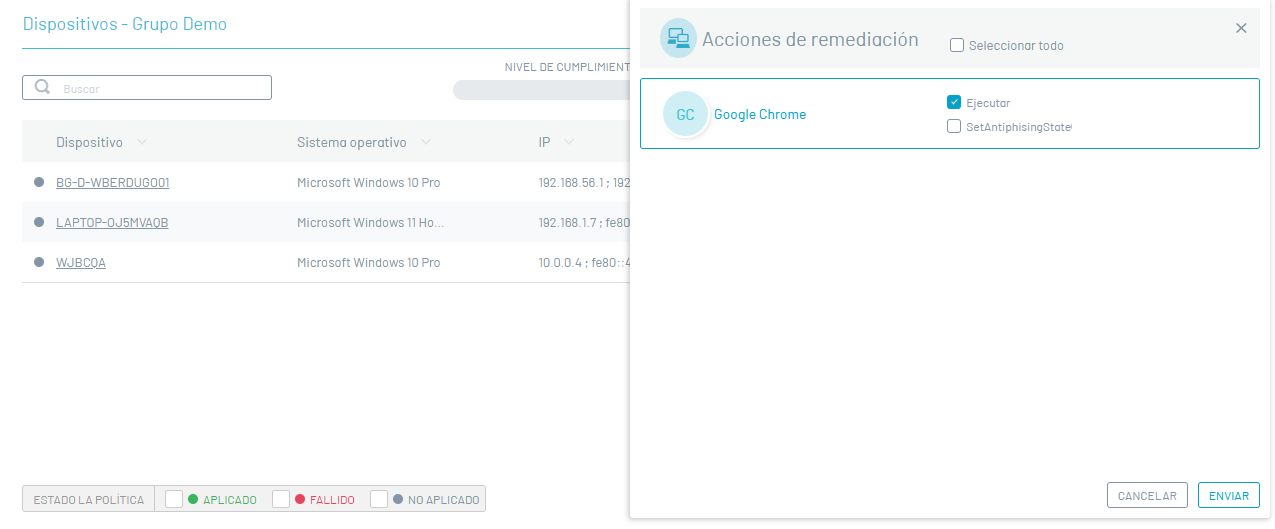
⚐ Note: When you select the Send The chosen remediation actions will be implemented.
⚐ Note: By selecting the menu option Compliance Groups in the list, only the remediations are performed in the options in the Group devices
7. Remediation actions that require a password require the management product key. These keys are required to access the advanced settings of the software.
The countryside Password It is not required and can be left blank, unless the product requires an administration key to make modifications.
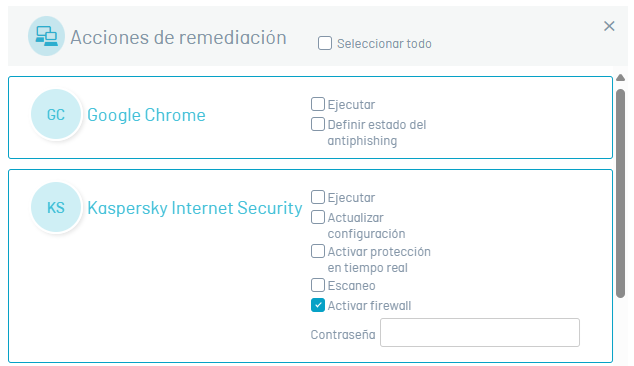
⚐ Note: Administration or Change Keys:
- 1. Required to make significant changes to software configuration or management.
- 2. They prevent unauthorized access and unwanted modifications.
- 3. Examples: Administrator keys in operating systems, root keys in Android mobile devices, keys to access advanced settings in security systems or business software.


