When you have the application created and have the data saved, you proceed to configure the application as follows:
How to set up authentication
1. You enter the Azure portal > Azure Active Directory > Menu > Application Logs > select the created application from the list that appears in the view.
2. In the Administer Search and select > Authentication then in Add a platform, select the Web.
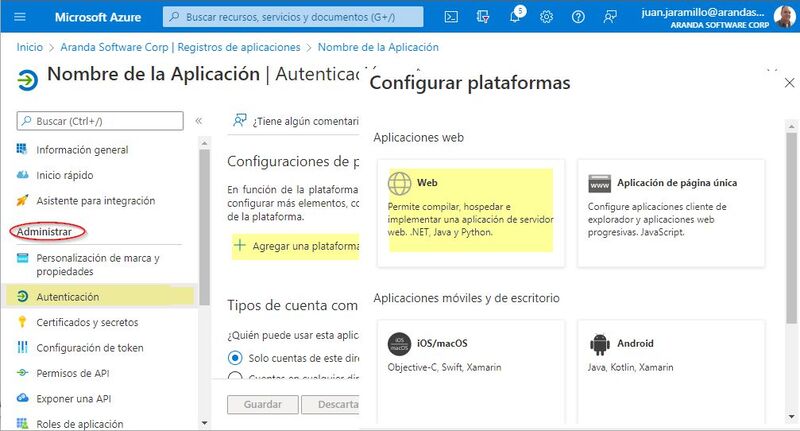
3. For the product Aranda Service Management ASMS fill out the Redirect URIs as follows:
- Output Server: https://[domain]/[SiteAdministration]/Main/Pages/OauthToken.aspx
- Input Server (Case Creator): (http://localhost) and perform the Manual token generation process (Postman).
- Replace the [domain] as appropriate, and then select Configure.
-
Replace [SiteAdministration] with the name of the directory or application of the administration site.
- Note: This name is case-sensitive and must be written as configured.
4. Para los demás productos Aranda, la UrI de redirección es: https://[dominio]/api/oauth2
Creation of the Secret
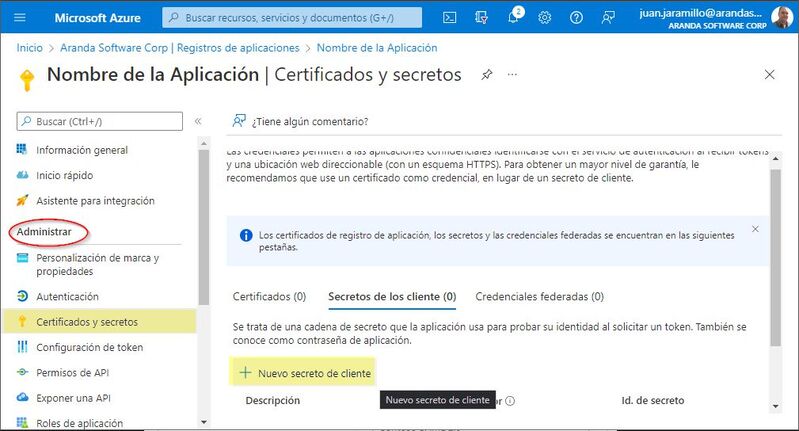
1. To create the secret, enter the Azure portal > Azure Active Directory > Menu > Application Logs > select the created application from the list that appears in the view.
2. In the Administer Search and select Certificates and secrets > Then click New client secret.
3. At the Hearing Add a client secret fill in the field Description, configure the Expires which corresponds to the duration of the secrecy. Then select Add (It is important to always keep this duration in mind since, when it expires, if it is not updated, authentication will fail.)
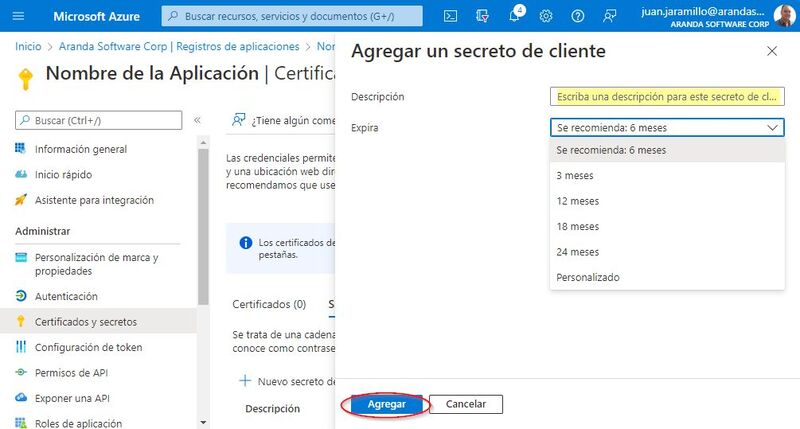
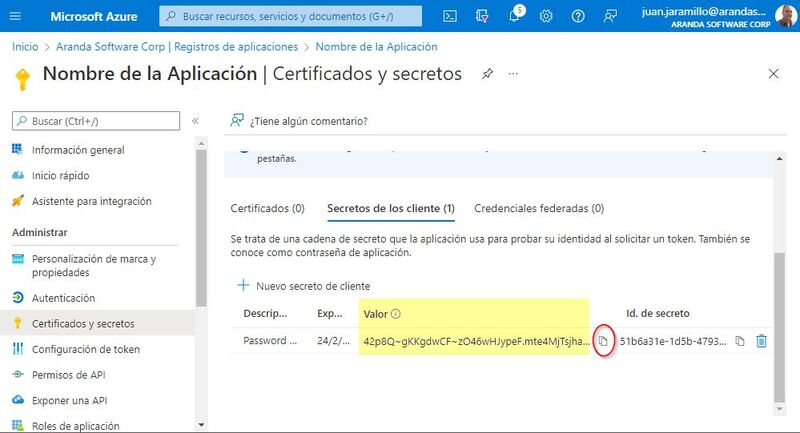
4. The value of the secret is only visible when it is created, so it must be saved for later use and retained for the configurations required in Aranda products.
- Client Secret Value -> Client Secret.
Configure API permissions
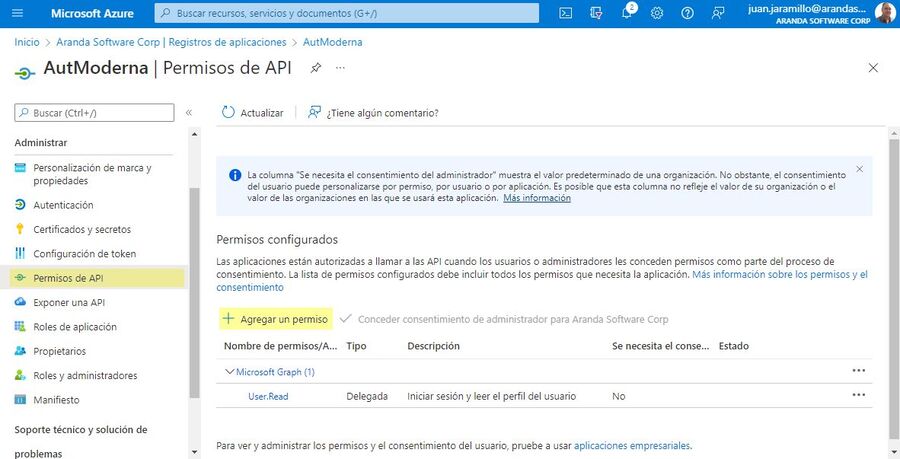
1. To configure API permissions, go to the Azure portal > Menu > Azure Active Directory > Application Logs > select the created application from the list that appears in the view.
2. In the Administer Search and select API permissions >Then click Add a Permission.
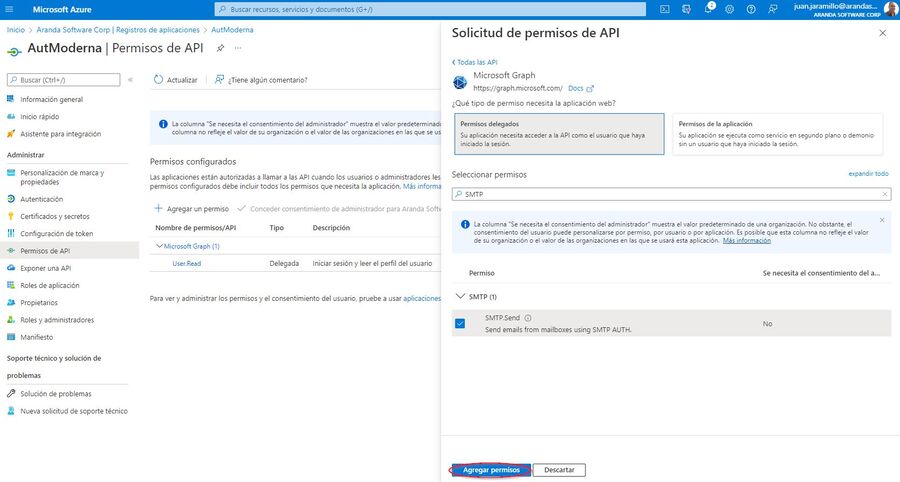
3. At the Hearing Request API permissionsselect Microsoft Graph > later Delegated permissions, Select the permissions according to your requirements: SMTP. Send (Sending mails), IMAP and POP (Reading emails). Click Add permission.
User and group settings
In this configuration, the email account(s) that will be able to access the application are associated.
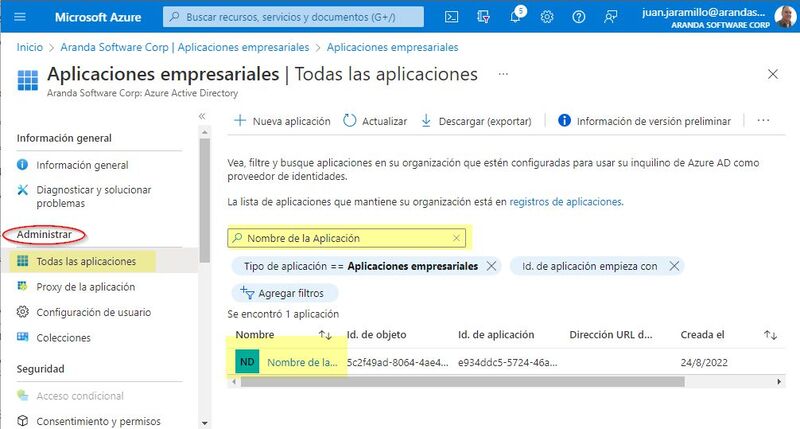
1. You enter the Azure portal> Menu> Azure Active Directory> Business Applications> select the created application from the list that appears in the view.
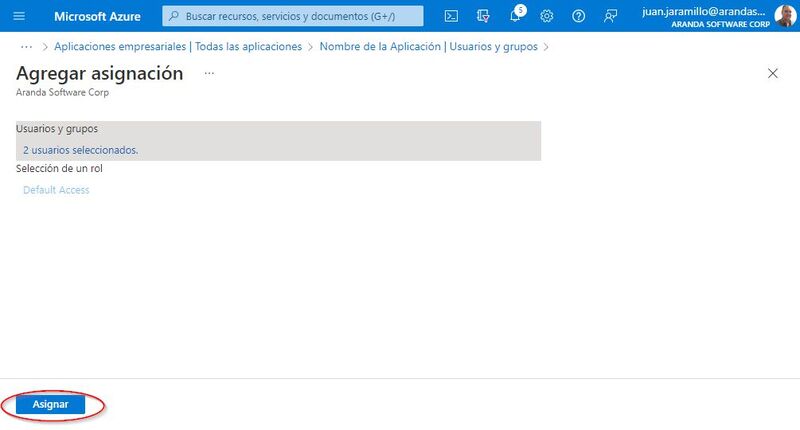
2. In the Administer Search and select Users and groups> and then Add User or Group.
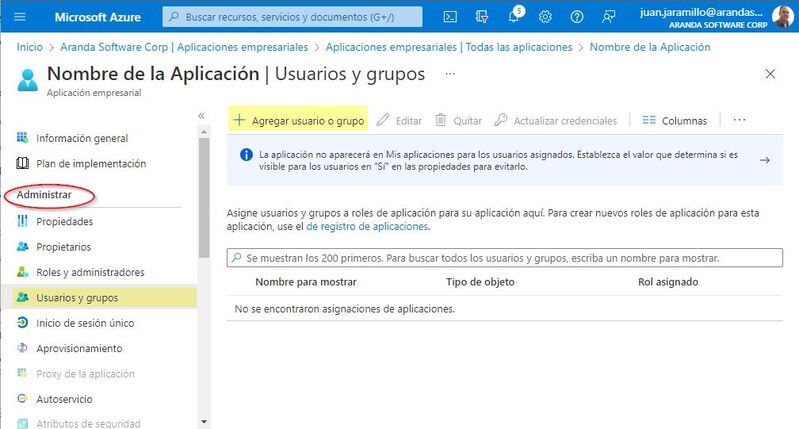
3. In the Add Mapping view, select None selected> Then look for the email account(s) you want to add, when you have all the emails selected click on Select.
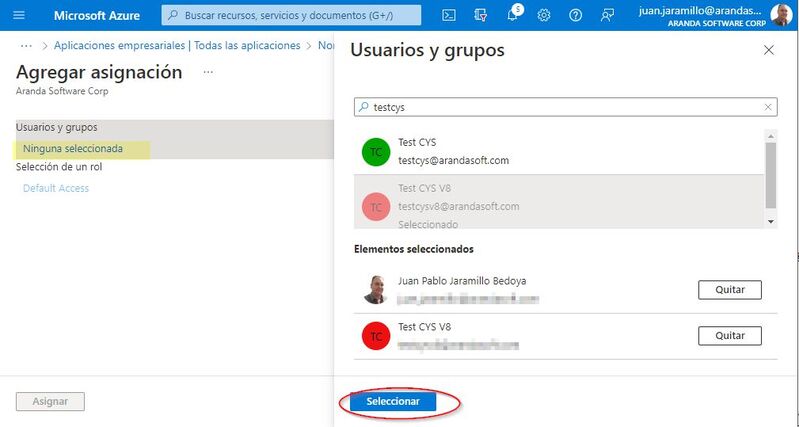
4. Finally select Assign.