Link
This section configures the options for linking devices to the AEMM server. The following can be filled out: properties:
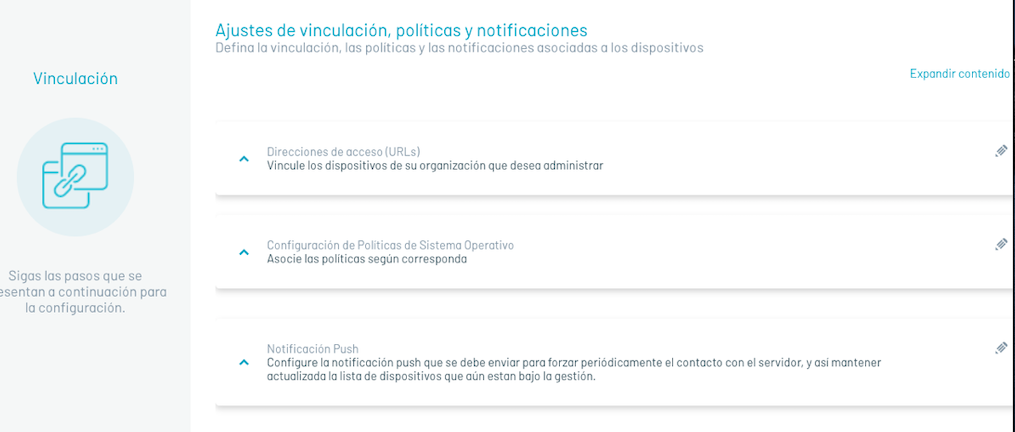
Communication Property:Access Addresses
| Fields | Description |
|---|---|
| MDM server access URL: | Url that will be used to establish communication between the devices and the AEMM server, the devices must be able to reach this url in order to link to the server. |
| Admin console url: | Url of the console from which the devices are managed and used to make linking invitations via email. |
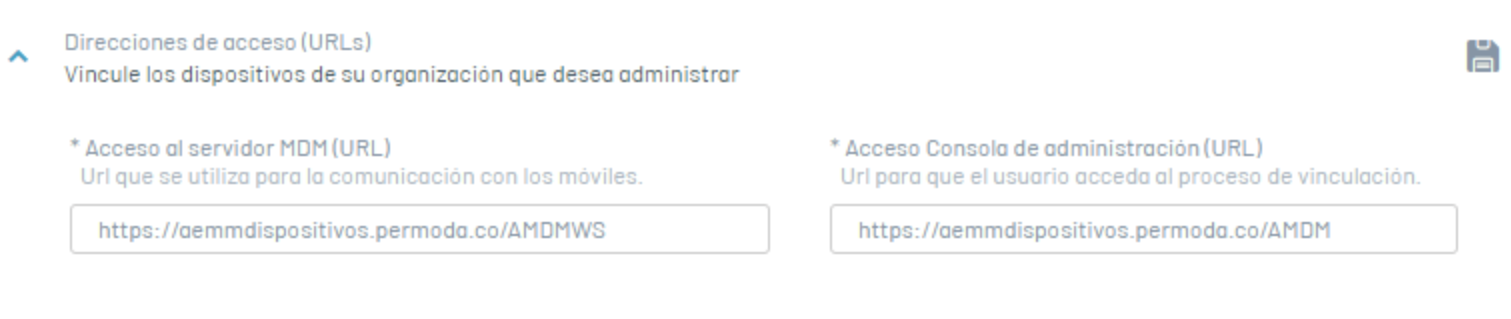
Device Configuration Property: Policy Configuration by Operating System
| Fields | Description |
|---|---|
| iOS Default Policy: | Policy that will be applied to iOS platform devices when they are paired. |
| Android Default Policy: | Policy that will be applied to devices on the Android platform when they are paired. |
| Default Policy Windows: | Policy that will be applied to Windows platform devices when they are paired. |
| Default Rule Set: | A set of rules that will be applied to any device that is linked. |
| “Request agent installation on iOS devices” checkbox: | A checkbox that, when checked, performs the action of sending the installation command automatically when an iOS device has performed web-type linking. |
Notification Settings Property: Push Notification
In this section you can configure the push notification that must be sent to the devices to periodically force contact with the server, and thus keep the list of managed devices updated.
To configure ping, fill in the following options:
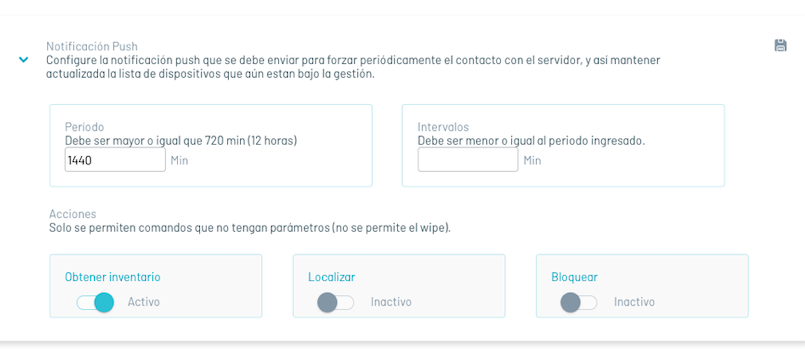
| Fields | Description |
|---|---|
| Period:: | Duration of a ping cycle to all devices. After this interval ends, all devices have received at least one push notification. |
| Intervals: | The number of device groups into which the total set of linked devices will be divided. This is so as not to queue all the push notifications at once, but based on this number of groups. |
| Actions: | Commands that will be queued before sending the push notification to each device, commands can be chosen from: Inventory, Location and Screen Lock. |
Once the above configurations have been made, click on “Save”, to persist and activate the ping mechanism.
Agent Profiles
This section presents the settings available for the “polling”, from the devices, which consists of every certain period of time the device by itself, without the need for a push notification, contact the AEMM server, looking for pending commands. Additionally This contact is server can be leveraged to deliver certain information configurable device status.
Creating an Agent Profile
To create an agent profile by clicking New
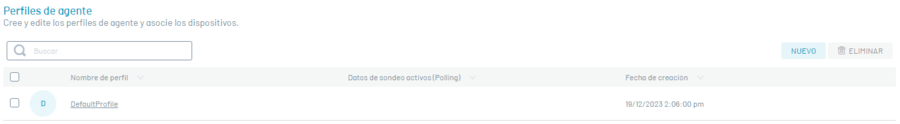
Fill in the following information and click on the Save.
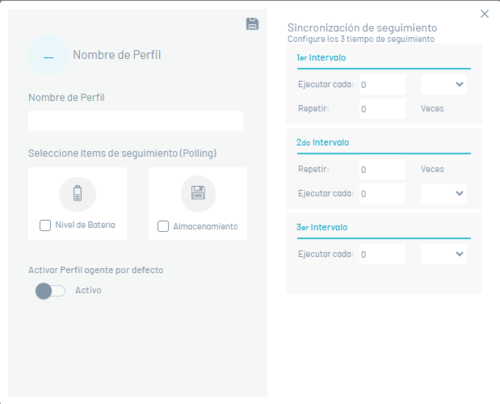
The fields presented correspond to the three consecutive stages of polling From devices:
| Fields | Description |
|---|---|
| First interval: | First stage, where you can configure the time interval and the number of times to run. |
| Second interval: | First stage, where you can also configure the time interval and the number of times to run. |
| Third interval: | Third stage, in which only the time interval can be configured, since this is the interval that will remain permanently once the first two stages have been exceeded. |
Associating devices to an agent profile
Click on one of the previously created rules and in the option that is enabled, click on the Associate devices button, where you can associate or remove devices to the rule.
ios
In this section, you can configure the corresponding options for iOS platform device management
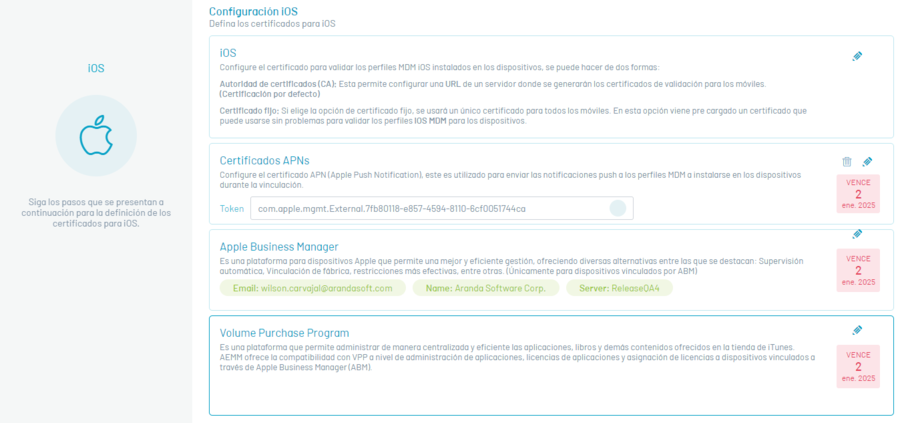
“iOS” section
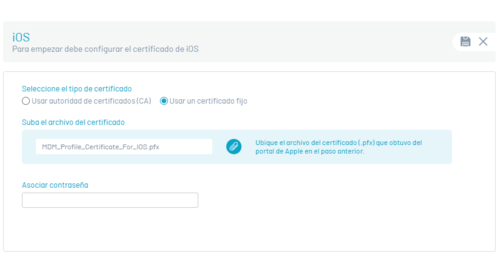
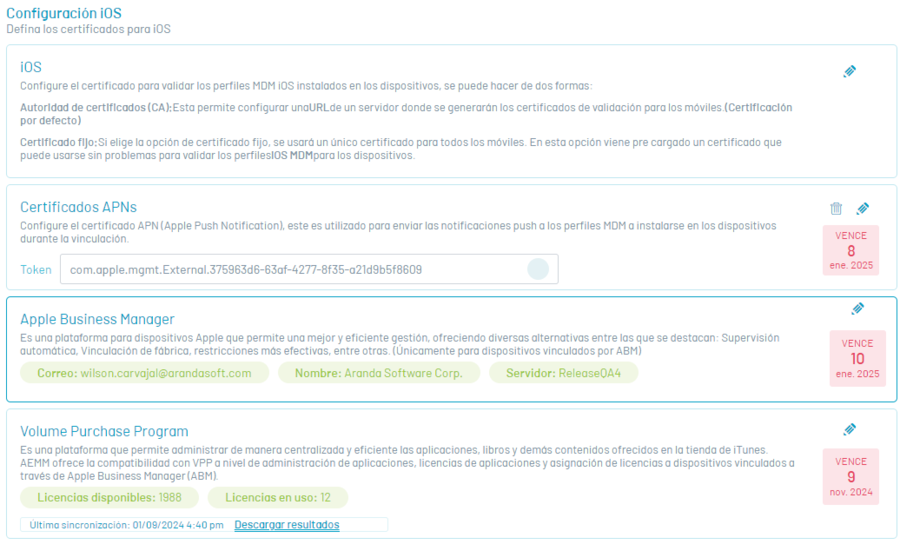
In this section, you can configure the certificate with which the iOS MDM profiles installed on the devices will be validated. To perform the configuration, click on the Edit option (pencil icon) to display the window where you can configure the certificate in two ways:
| Fields | Description |
|---|---|
| Using Certificate Authority (CA): | This option allows you to configure a URL of a server where validation certificates will be generated for mobiles. |
| Fixed certificate: | If you choose the fixed certificate option, a single certificate will be used for all mobiles. A certificate comes preloaded in this option that can be seamlessly used to validate iOS MDM profiles for devices. |
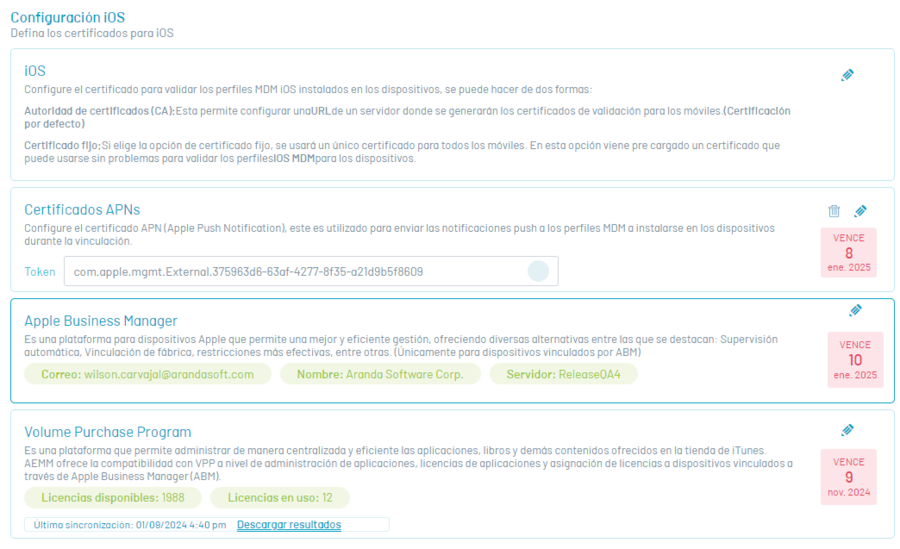
APNs Certificate Section
In this section you will be able to configure the APN (Apple Push Notification) certificate, used to send push notifications to MDM profiles to be installed on devices during pairing. To perform the configuration, follow these steps:
Creating a New APN Certificate
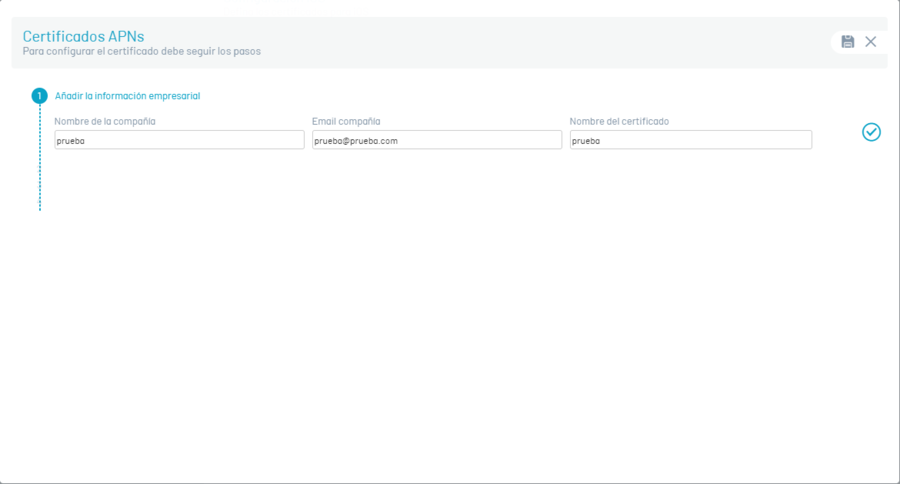
Log in to APNs certificate and click New
Enter the name and email of the company, plus the name of the certificate and then click on Continue (check icon).
The CSR file that you need to save is then automatically downloaded. This CSR file changes each time this process is performed; it is recommended that you complete the APN configuration process with the same CSR file.
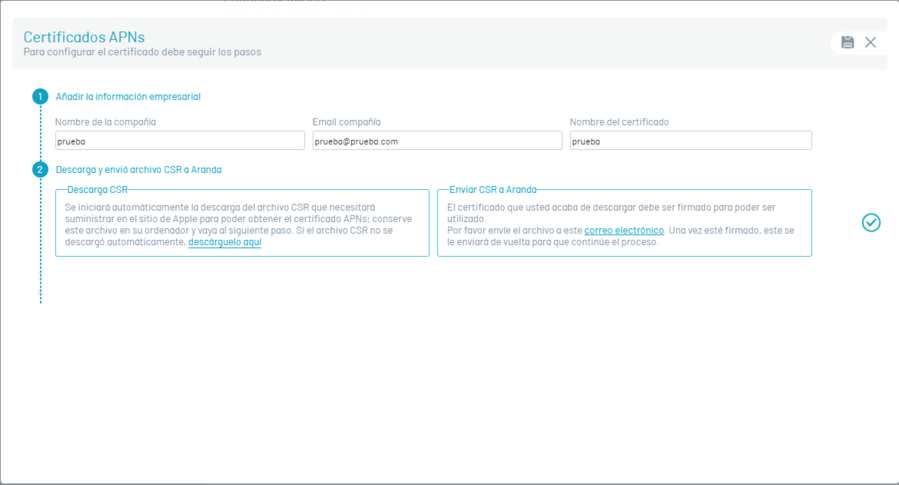
Send the CSR file to your representative in Aranda via email and click on the check icon corresponding to step 2.

Go to the Apple page to generate the APNs certificate
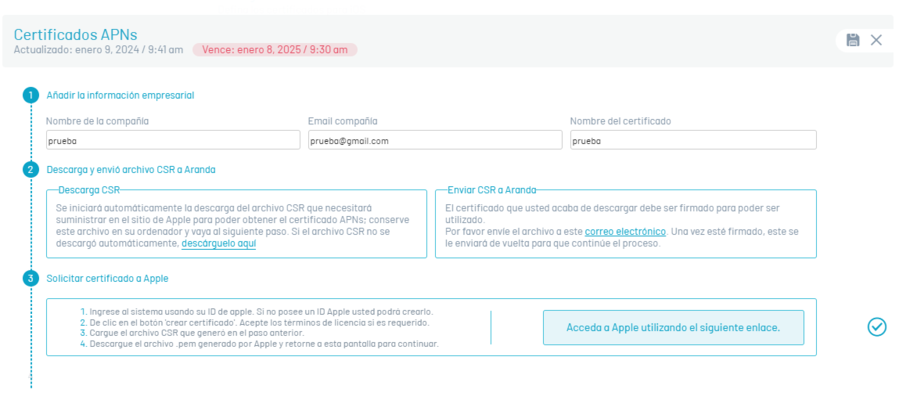
Enter your Apple ID and password
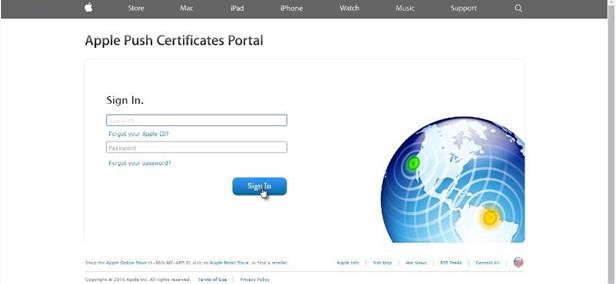
Click on the option Create certificate
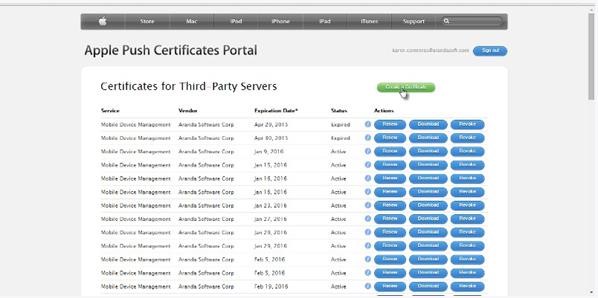
Agree to terms and conditions.
Select the “PLIST” file, which you received by email from the representative in Aranda.
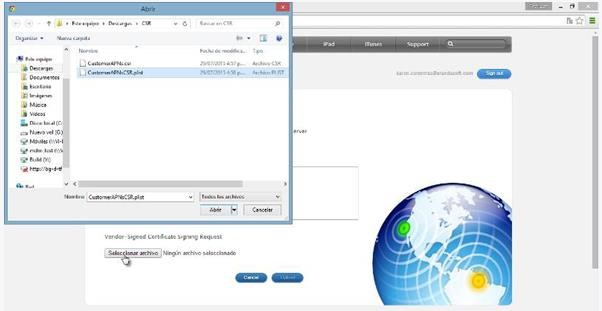
Write a brief description of the certificate being created, with the goal of identifying it in the future. Download and save the PEM file that is generated.
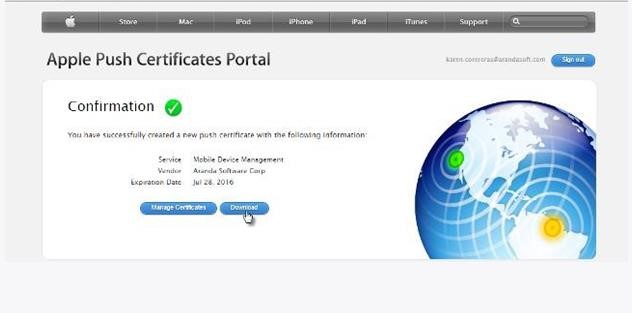
Continue within the console and then click on the check icon corresponding to step 1 and attach the “PEM” file that was generated in the previous step.
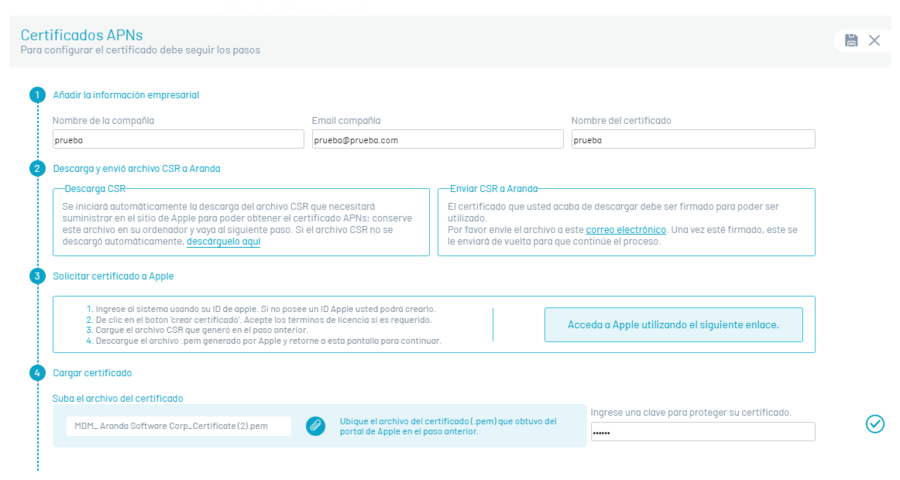
In the Upload Certificate Click on the check icon corresponding to step 4.

The certificate must be successfully uploaded.
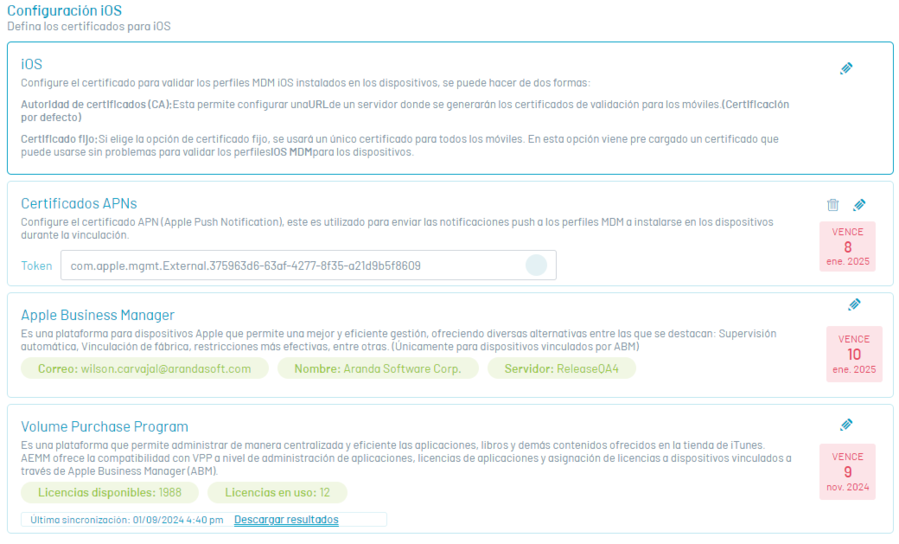
The certificate created and uploaded to the AEMM server will be valid for one year, counted from its generation on Apple’s APN Push Notification platform.
This certificate is associated with subsequent bindings of iOS platform devices as it cannot be replaced with a new certificate, which would result in the isolation of the devices from the AEMM server and their consequent inability to receive and process commands.
This created certificate has to be renewed before its expiration and for such when it is created a system alert is placed that makes a reminder one month before the expiration of the certificate.
If the renewal procedure is not done in time, it will cause an effect similar to that of changing the certificate for a new one, which is the total and irreversible isolation of the devices already linked and that use this APN certificate.
The following section details the APN certificate renewal process.
Renewing a previously created APN certificate
Run the first 5 steps of the above process (Creating a New APN Certificate) and then do the following:
Once on Apple’s APN platform, locate the certificate record in question and click “Renew.” To identify the record in question, you can use the short description entered at the time of its creation, this in case you have more than one record in your APN account.
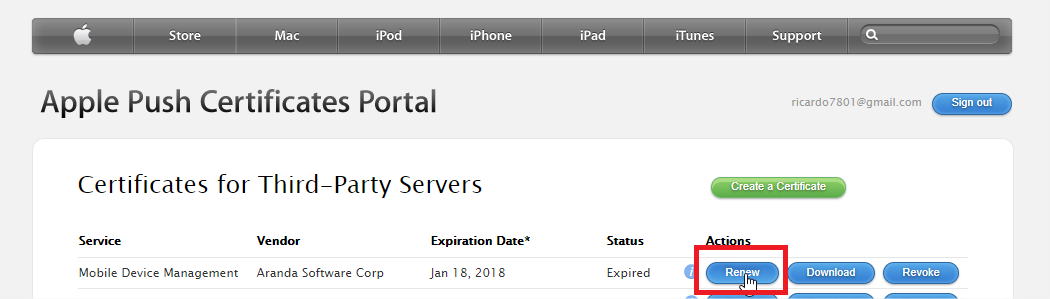
Next, execute steps h, i, j, k, l, m of the previous numeral, to complete the process.
The renewed certificate will have the same validity period of 1 year and must also be renewed before it expires, so as not to reach the consequences already described.
APN Certificate Validation
In the APN renewal (update) process, the configured APN must match the new APN file to be updated and you can view it from the Apple console where you created and renewed the certificate (https://identity.apple.com/pushcert/ ). In authentication, enter the same email with which the certificate was created.
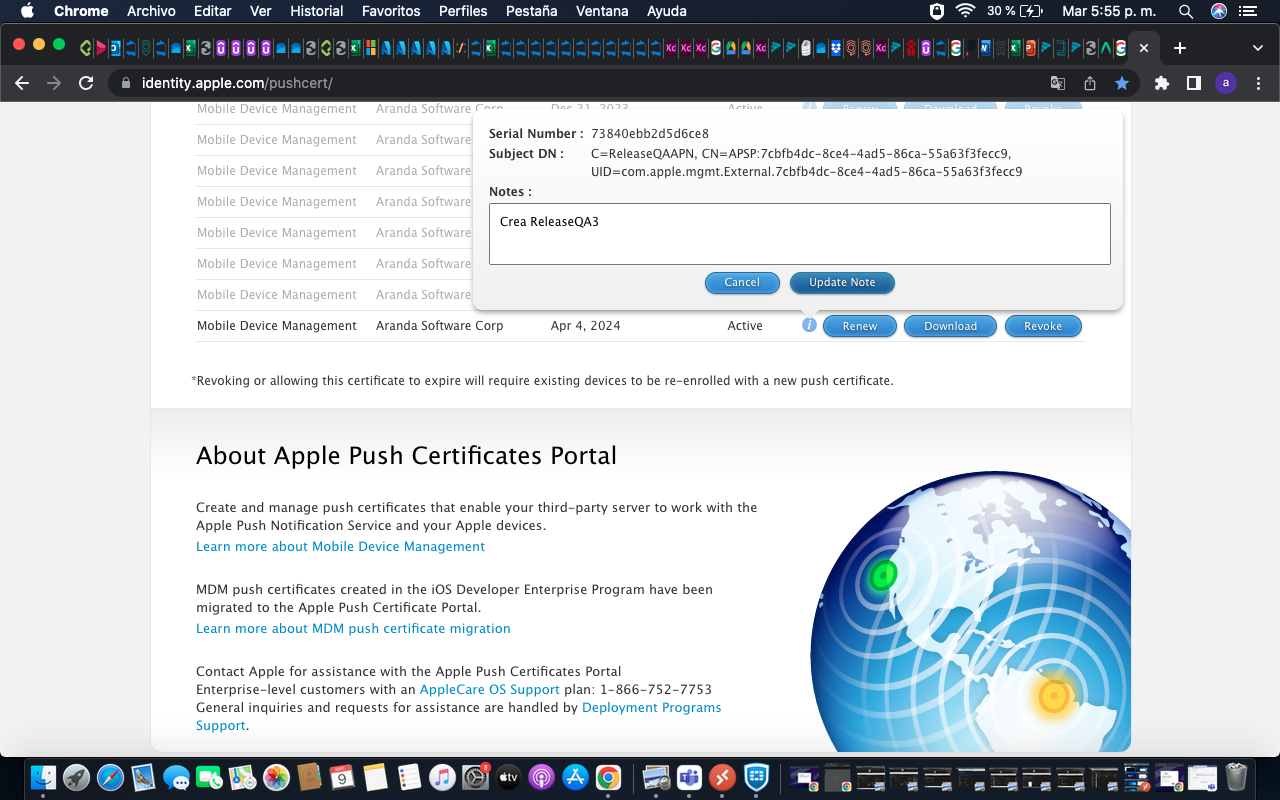
When you select the record, in the information icon, it will show you the following data: serial number and subject DN; the latter item in the UID tag: (com.apple.mgmtExternal.XXXX, as shown in the image)
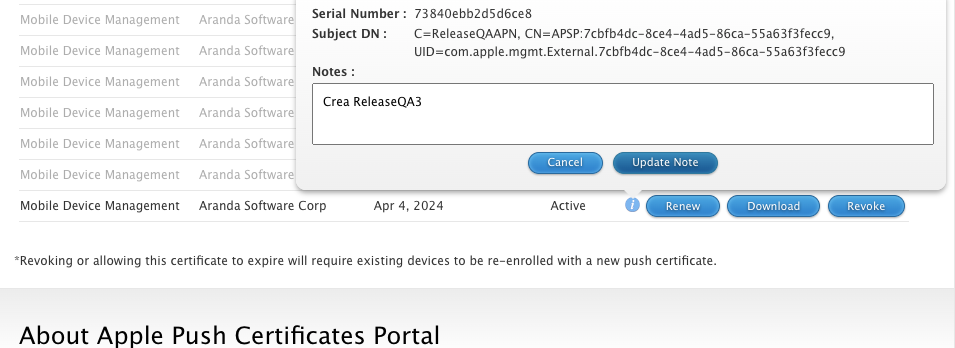
This information must match the profile information found on the linked devices, as described below:
1- Select a linked device before performing the APN update.
2- On the device go to the settings option ->Device Management and VPN->Aranda MDM Profile-> More details-> Mobile device management-> Topic1
Viewing the APN theme on iOS devices
| Field | Description |
|---|---|
| Settings | 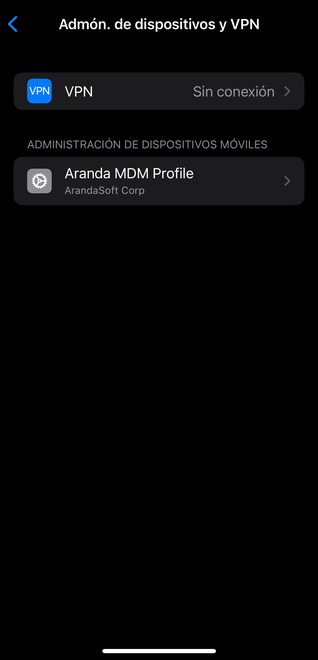 |
| Settings | 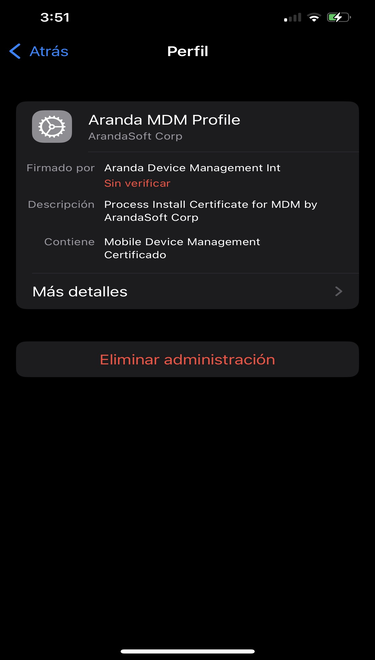 |
| Settings | 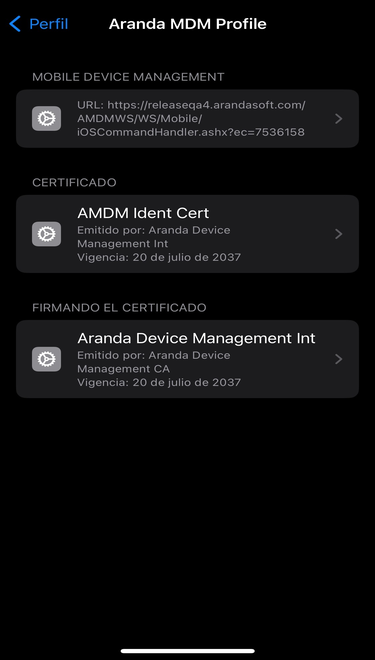 |
| Settings | 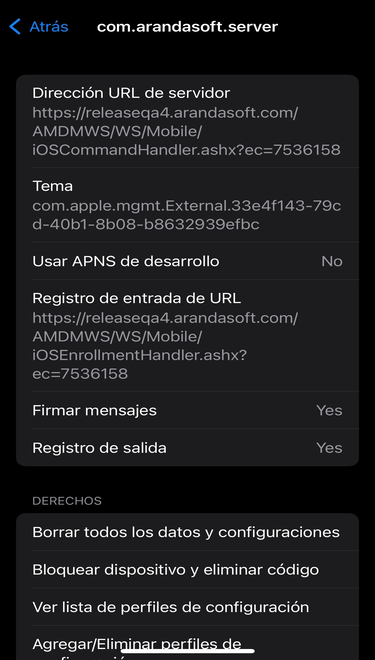 |
Apple Business Manager (ABM) section
Apple Business Manager is a platform for Apple devices that allows better and efficient management, offering various alternatives among which are: Automatic supervision, Factory linking, more effective restrictions, among others.
To activate this functionality, it is necessary to have a current account on the Apple Business Manager platform (https://business.apple.com/) and perform the following steps:
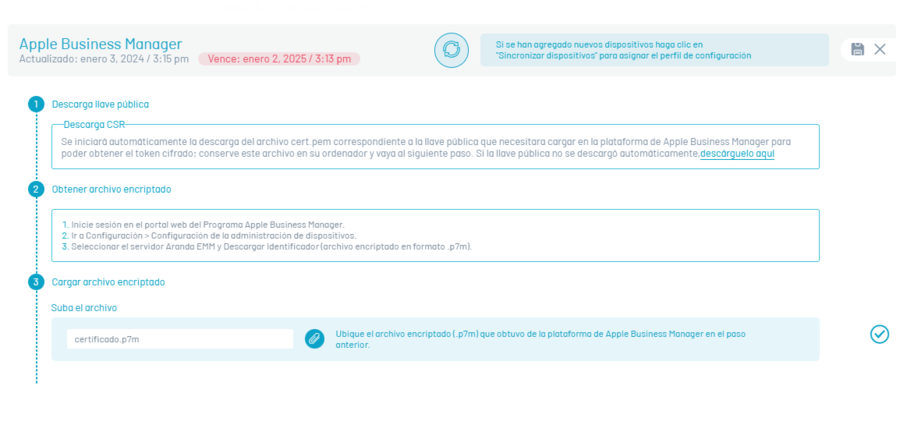
Navigate to the Apple Business Manager section and click New
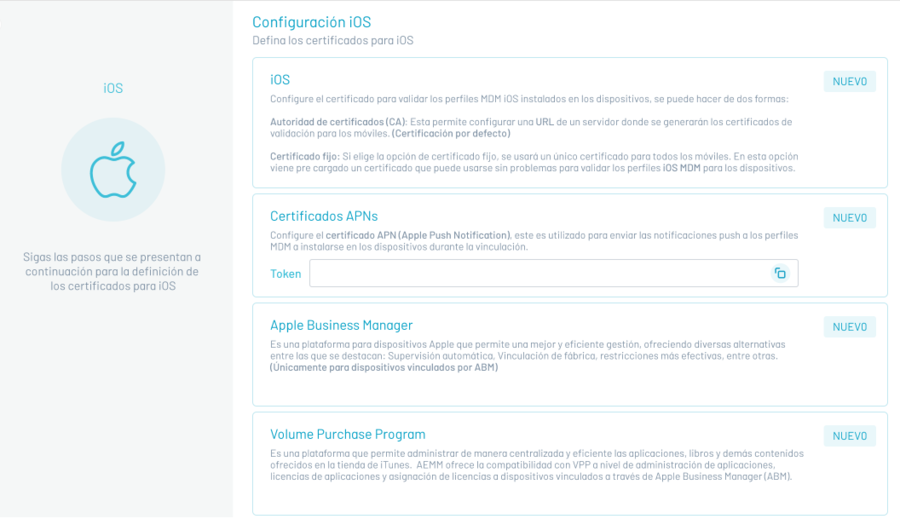
Save the cert.pem file that will uniquely identify the AEMM server instance. Save it in a safe place and click on the check icon corresponding to step 1.
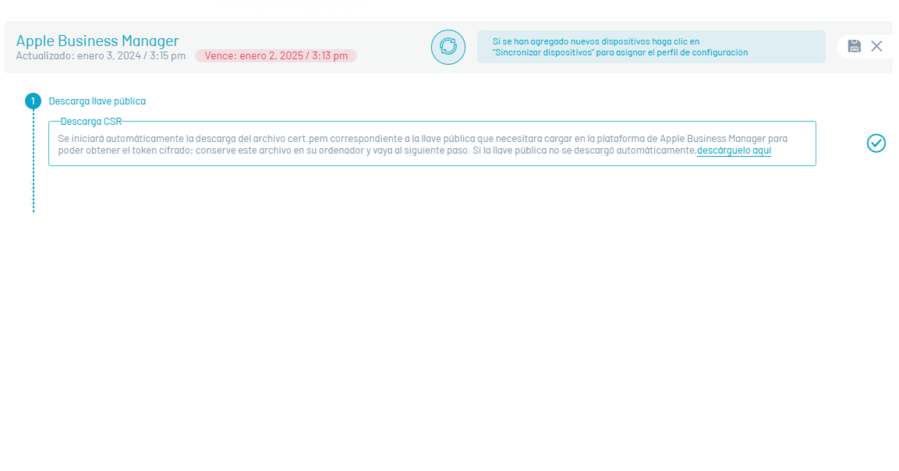
The following are instructions for pairing the AEMM console with the public key downloaded in the previous step in the Apple Business Manager Admin Console.
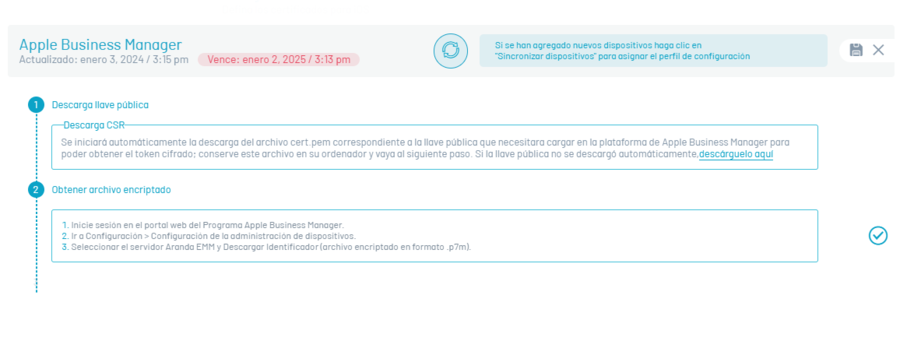
Select Save and to finish downloading the file with extension p7m in the Download identifier.
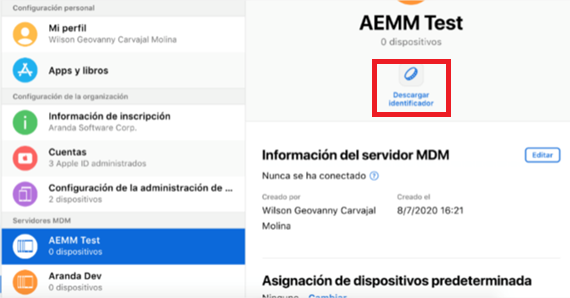
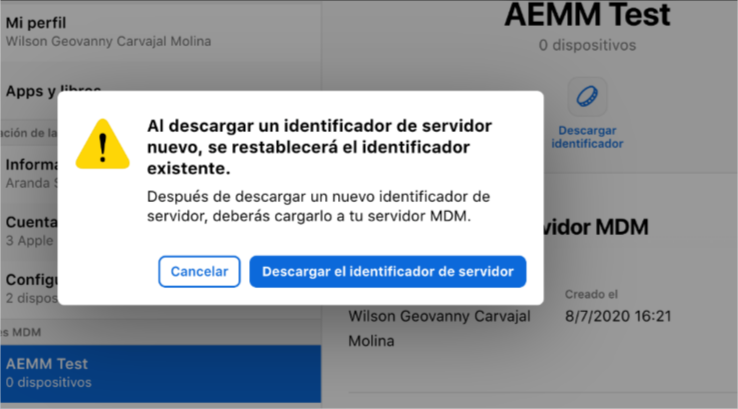
In the AEMM console, click the check icon for step 2 and upload the p7m extension file downloaded from the Apple Business Manager Admin console to the AEMM console. Upload the p7m extension file.
After selecting the file, click on the check, corresponding to step 3.
Volume Purchase Program (VPP) Section
Apple’s Volume Purchase Program is a platform that allows you to centrally and efficiently manage the applications, books, and other content offered in the iTunes store.
AEMM offers VPP support at the application management level, application licensing, and assigning licenses to linked devices through Apple Business Manager (ABM).
To link the AEMM server with VPP, perform the following actions:
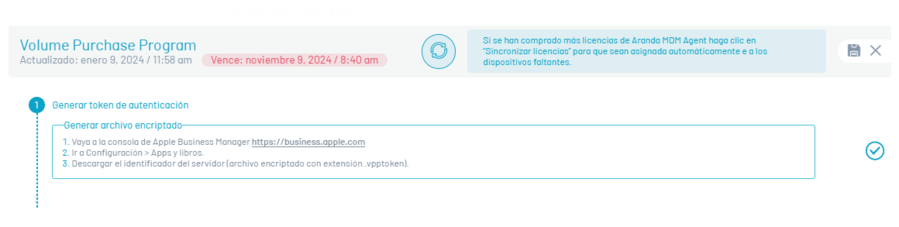
In the Volume Purchase Program section, click New
According to the instructions presented, enter the Apple Business Manager console, to generate the authentication token.
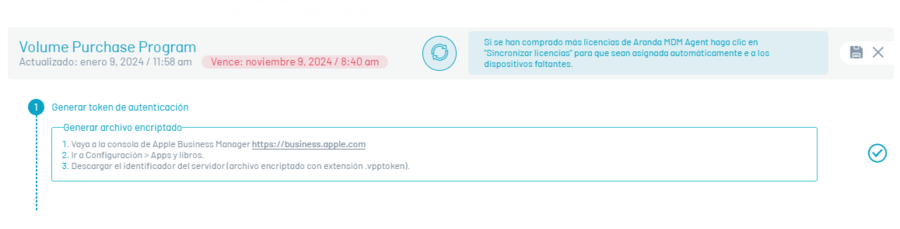
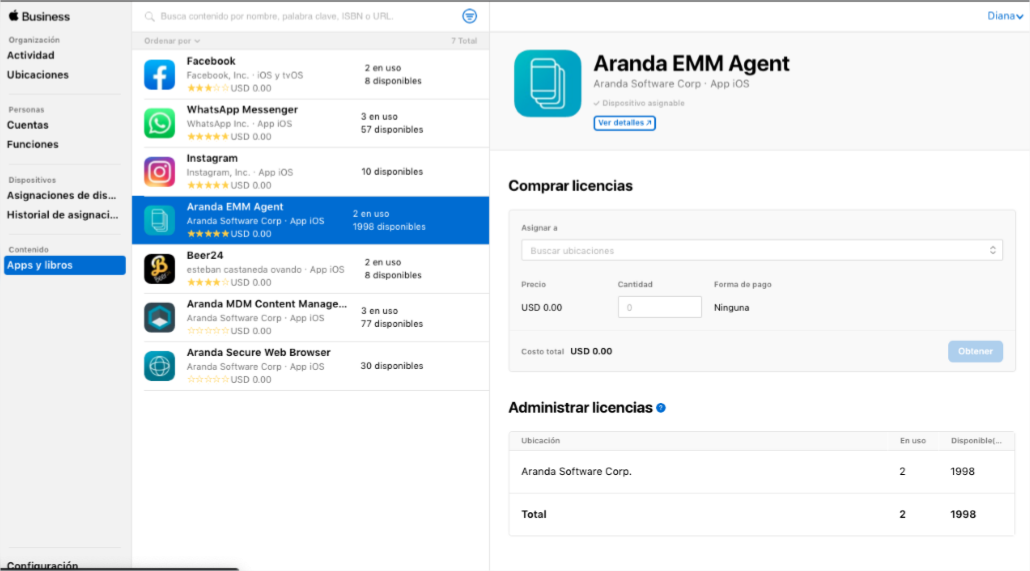
Once inside the ABM Management Console, go to the option Configuration > Apps & Books, there you will see the identification of the configured servers; Click Download.
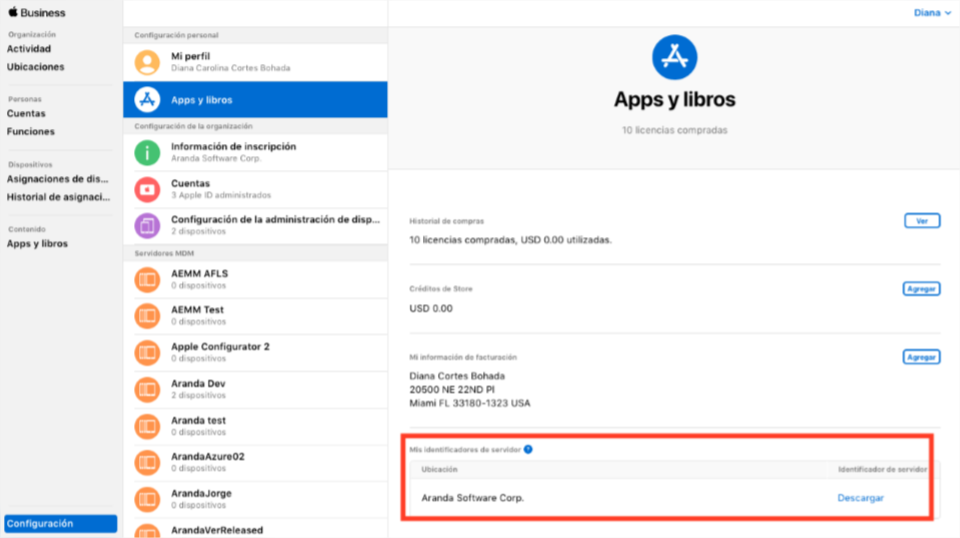
Save the downloaded file to a safe place, log in to the AEMM console, and click the check icon for step 1.
Upload the downloaded ABM console file from the previous step, click the button, and upload the file.
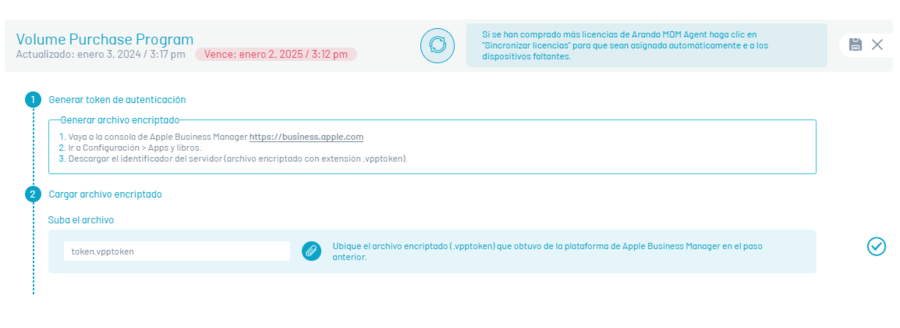
Click on the check icon corresponding to step 2 to finish the process.
To perform the license synchronization process, in the Volume Purchase Program Click the Edit and in the window that is enabled, click on the Sync licenses. The system will automatically assign AEMM Agent for iOS licenses to devices that are linked by ABM.
Finally, you will see data corresponding to Aranda EMM licenses, such as their status (available and in use), the date of enrollment of the VPP and their expiration. Remember that the licenses have a duration of 1 year.
There is also an option to download a results file, which indicates which devices have been assigned the license and which have not.
On AEMM console:

On ABM console – VPP
Things to keep in mind:
- Before synchronization is performed, licenses must be available from the application of Aranda EMM in ABM for devices that are going to assign.
- The Aranda EMM Agent application must be imported into the applications from the AEMM console.
Android for work
In this section, you can configure the options needed to enable support for the enterprise work environment for Android devices, called Android for Work (AFW) or Android Enterprise.
“Android For Work” tab
Android For Work or currently called Android Enterprise is an Integrated Infrastructure and Platform for the management of Android devices, created by Google.
AFW offers application-level device management capabilities, restrictions, and settings that allow AEMM to have greater control over devices on the Android platform.
To use AFW in AEMM, the following steps must be followed:
Enter the AEMM Home console, in the heading menu select the option Configuration. In the *Main Menu Preferences: Select the option Mobile and Android.
Description
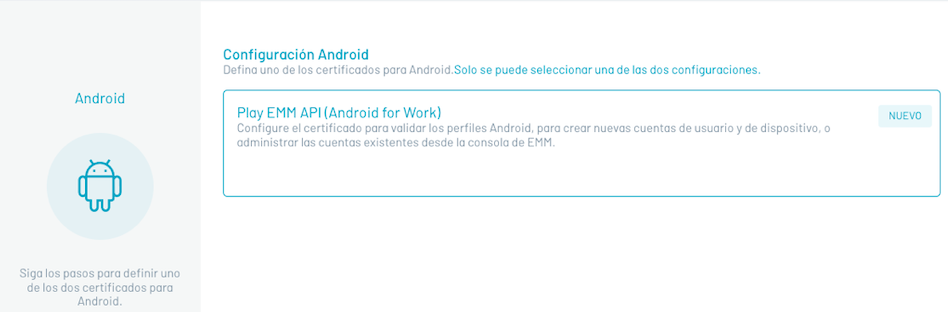
Turn on the Android for Work setting as shown below.
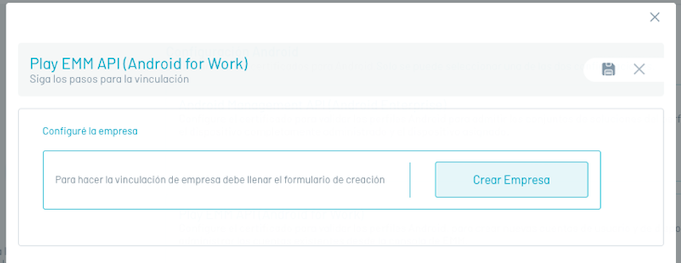
Follow the google activation guide.
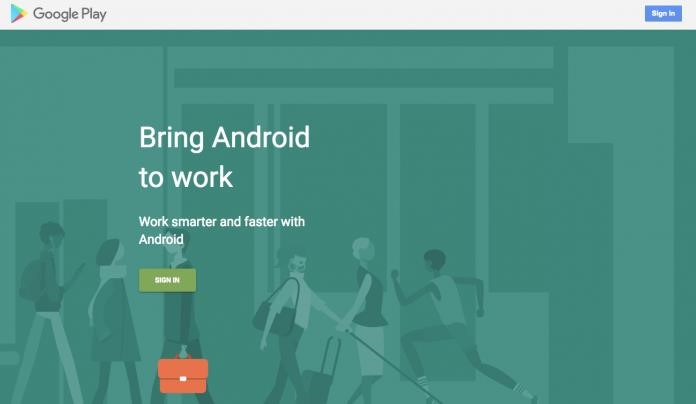
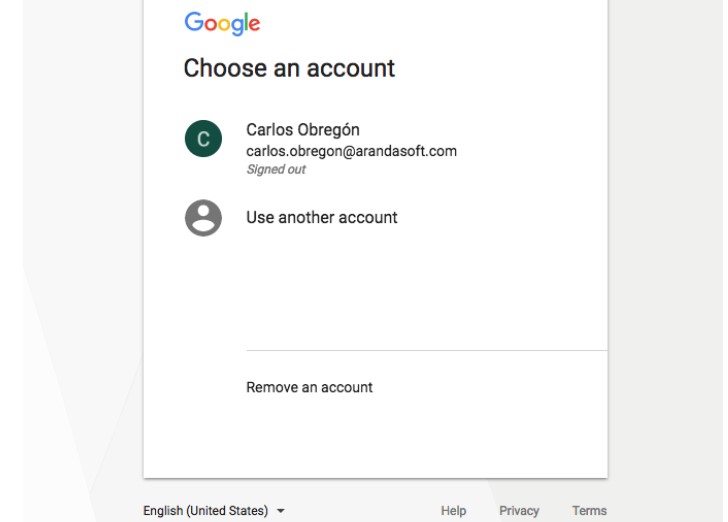
Within this activation, an administrator account of the organization.
With this you must log in to register with Android For Work.
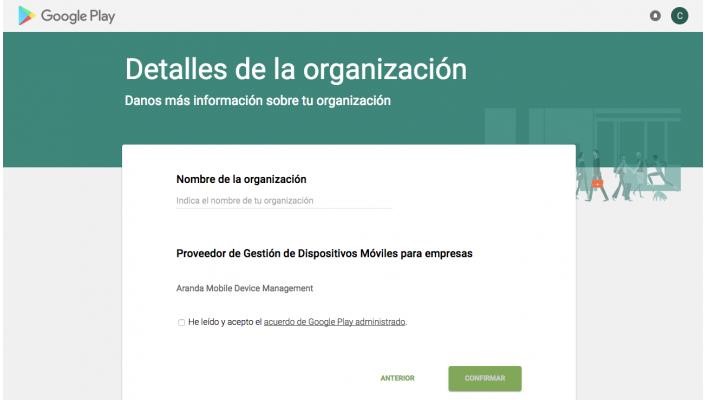
Then fill out the registration form requested by google and confirm the registration
If the process is successful, the EMM console should look like this:
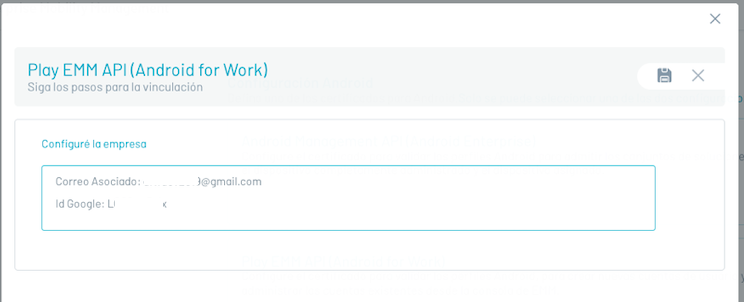
Click on the save icon, the system displays the related mail and the Id assigned to the console by google:
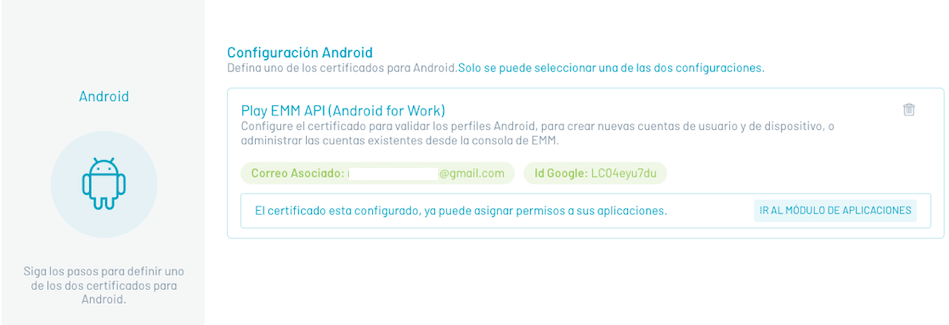
Once your console is registered with Android for Work, the following options are presented:
- Go to the Applications module: Navigate to the Applications section where you can Initiate application management operations against Android for Work.
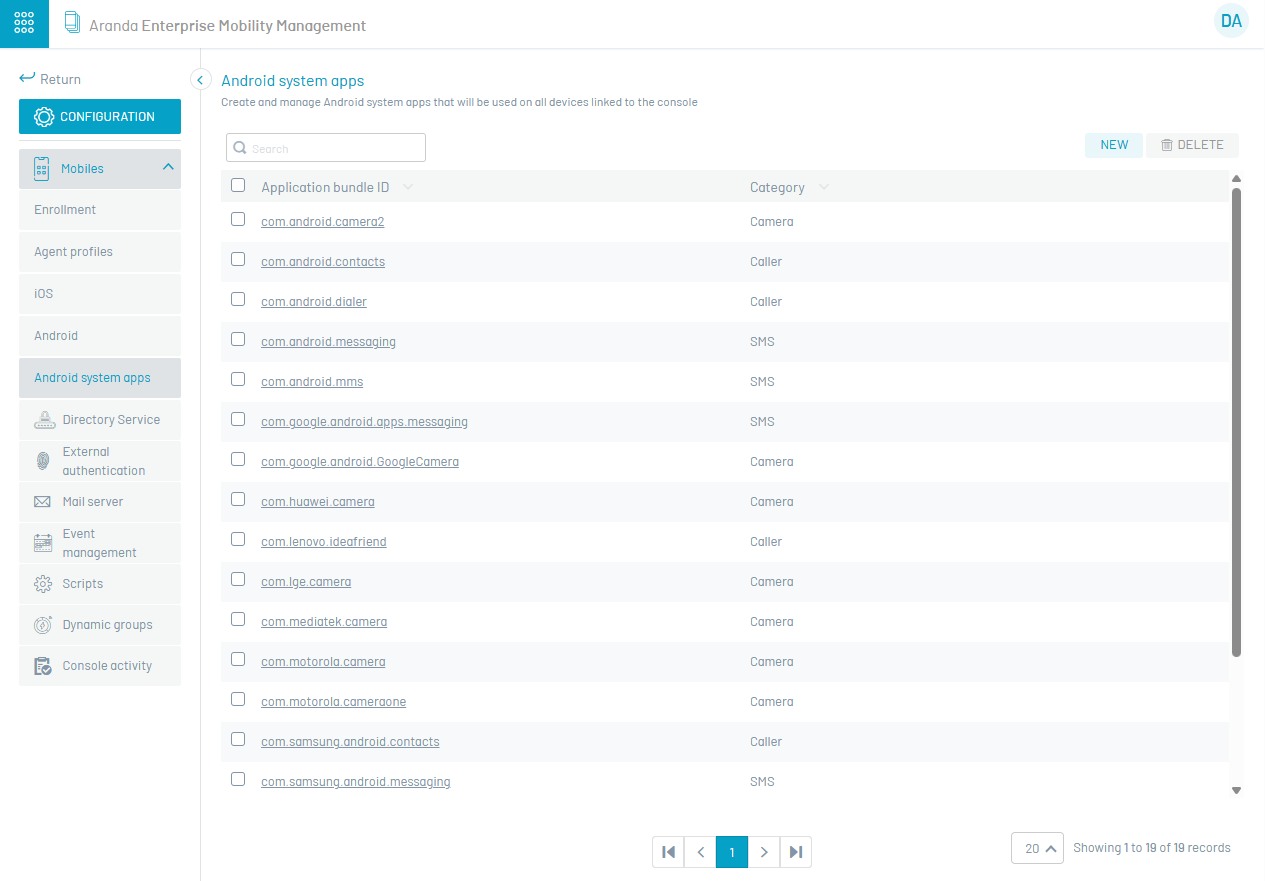
Android System Apps
In this section, the administrator can manage the applications that are installed on the device but are not displayed; that is, on some occasions when the user is linked, it detects that the camera is not visible (example). The following is a step-by-step description of how to perform this action:
1. In this case, the name of the required package is identified (by means of the hidden packages command-device module). 2. This bundle id must be entered in the Android System Applications option.
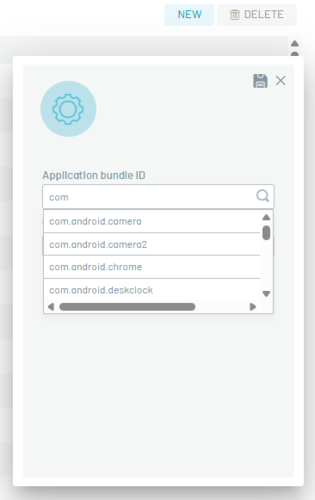
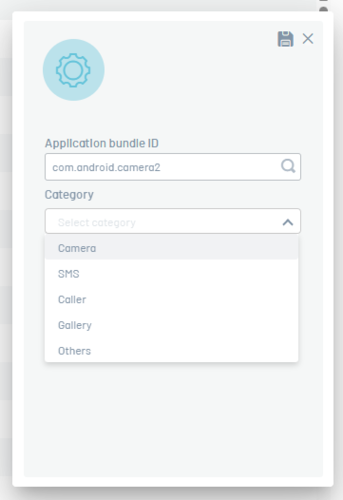
To configure a new package, click on New and then fill in the application Bundle ID and Category data, to persist the information click on Save.
To edit an existing package, place it in the package list and update its data, then click Save.
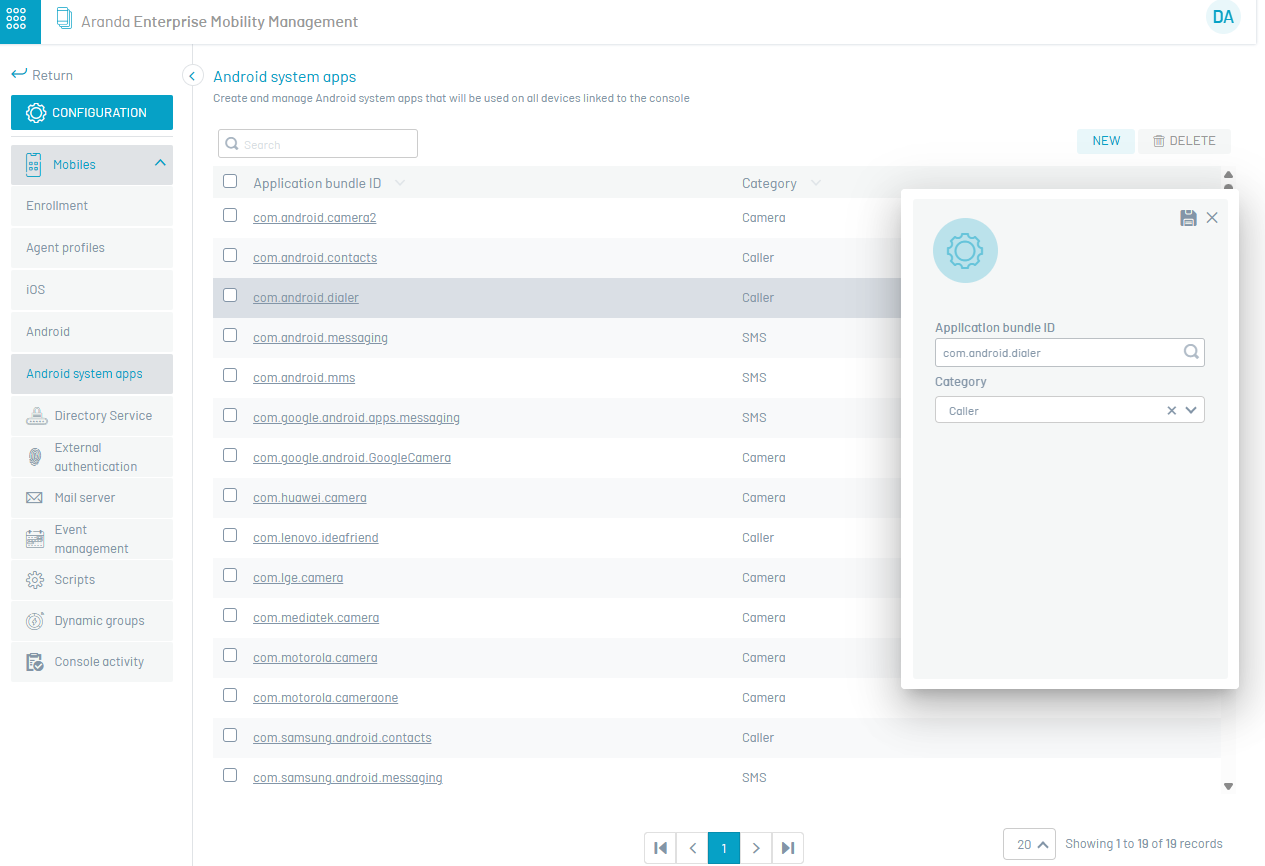
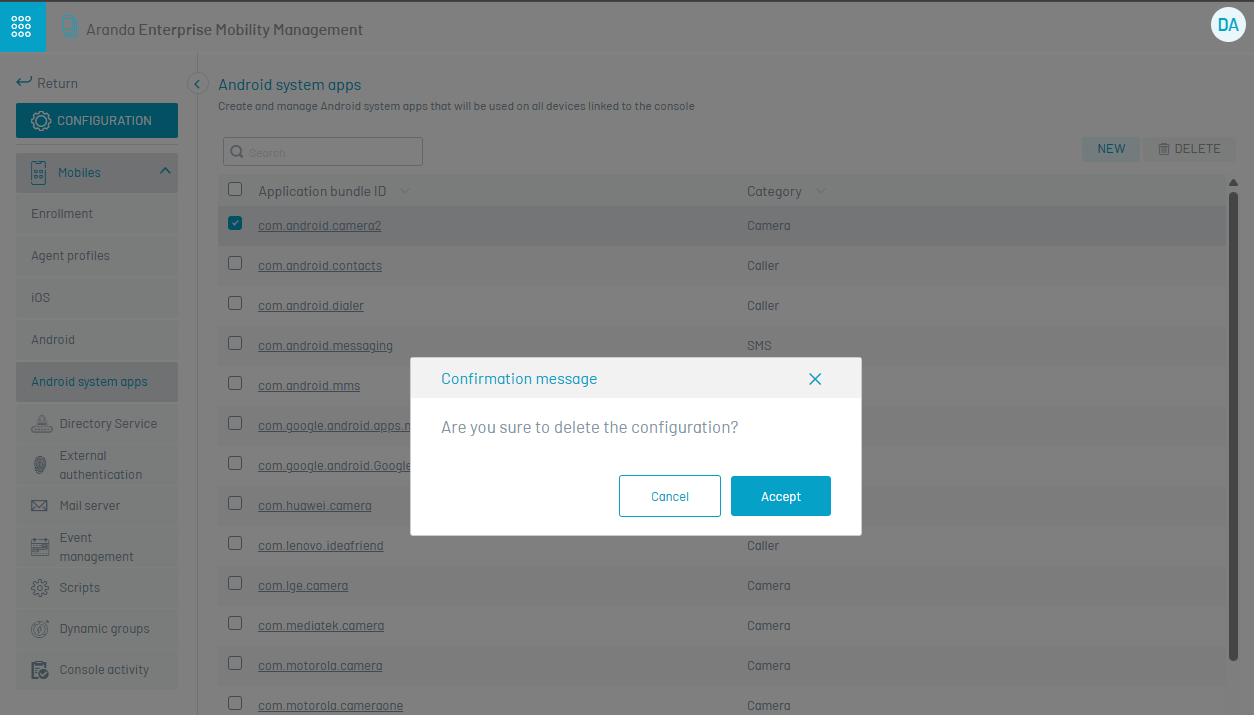
To delete a package, click the delete icon in the package registry.
3. After entering the package name in the console (bundle id), a politics by activating the System Applications category in the Applications section or/and in the Kiosk section of the Policy module. The added packets will be sent to the devices as part of the policy that includes the items already named.
The device will “uncover” the applications corresponding to the package names configured here and the user will be able to see the application that is hidden.
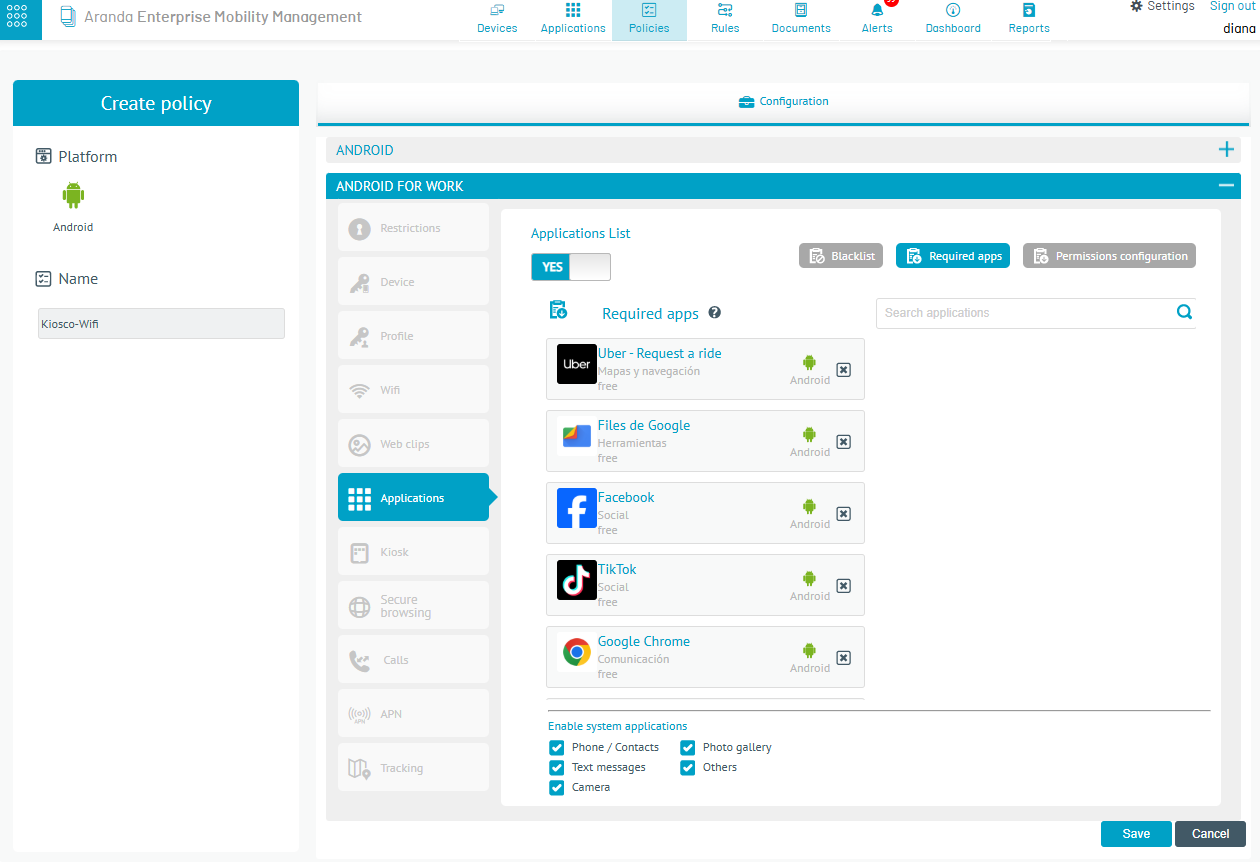
⚐ Note: - For android system apps:
- You should note that this option is only handled in AFW Device Owner (DO) pairing mode


